This article highlights the primary ways in which enterprise Accounts Payable (AP) teams are being targeted by criminals through payments and invoicing fraud attempts in 2022. After reviewing the most common forms of fraud being perpetrated against AP teams today, the article concludes by highlighting five of the leading tools and strategies that enterprises can adopt to help their AP teams prevent and detect fraud.
AP Teams Are On the Front Lines of Defense Against Numerous Forms of Fraud
Given the absurdly high volume of fraudulent payment and invoicing schemes that are being perpetrated against the corporate environment in 2022, it’s safe to say that virtually every financial department within a modern enterprise faces its fair share of security threats.
When it comes to high-value corporate ACH and wire payments, it is often the CFO or treasury group that criminals target most frequently. Looking back over the past few years (especially during the Covid “WFH” era), we have seen a multifaceted array of phishing, business email compromise (BEC), and other malware or ransomware schemes being attempted in record numbers, from both external and internal sources, with a surprisingly high success rate.
However, in addition to treasury and the CFO, data shows that many Accounts Payable (AP) teams – particularly within large, global companies – are also targeted in high propensity, often through fraudulent invoicing, billing, and payment processing.
Depending on any single company’s size and composition, the AP department may consist of 1-30 individuals, and may process a few dozen or several thousand invoices every month. There is often a vendor relationship aspect attached to the AP function as well, provided that invoices are paid on time. As AP groups go about managing their roles, the main benefit to their organization is that outstanding payment requests are effectively fulfilled without violating deadlines or contracts. Additionally, an optimized AP group can help take advantage of early-pay discounts or other types of incentives to earn additional revenue, and can also help identify fraudulent invoice requests and other security threats. For enterprises making hundreds or thousands of payments every week, these benefits are essential.
However, for organizations that do not take the security aspect of AP’s role seriously or that fail to adequately train and prepare AP teams to identify and prevent fraudulent attempts, the effects of a successful attack can be severe.
What are the Primary Types of Fraudulent Threats That AP Teams Face?
Over the past few years, there have been three main types of AP fraud commonly perpetrated – each of which consists of a subgroup of similar schemes that criminals use to extract funds. Depending on the nature of the scheme, attacks can be carried out by company employees acting illicitly from the inside, or from tech-savvy fraudsters operating remotely from entirely different countries or continents.
Let’s quickly review these three main categories of AP fraud in more detail.
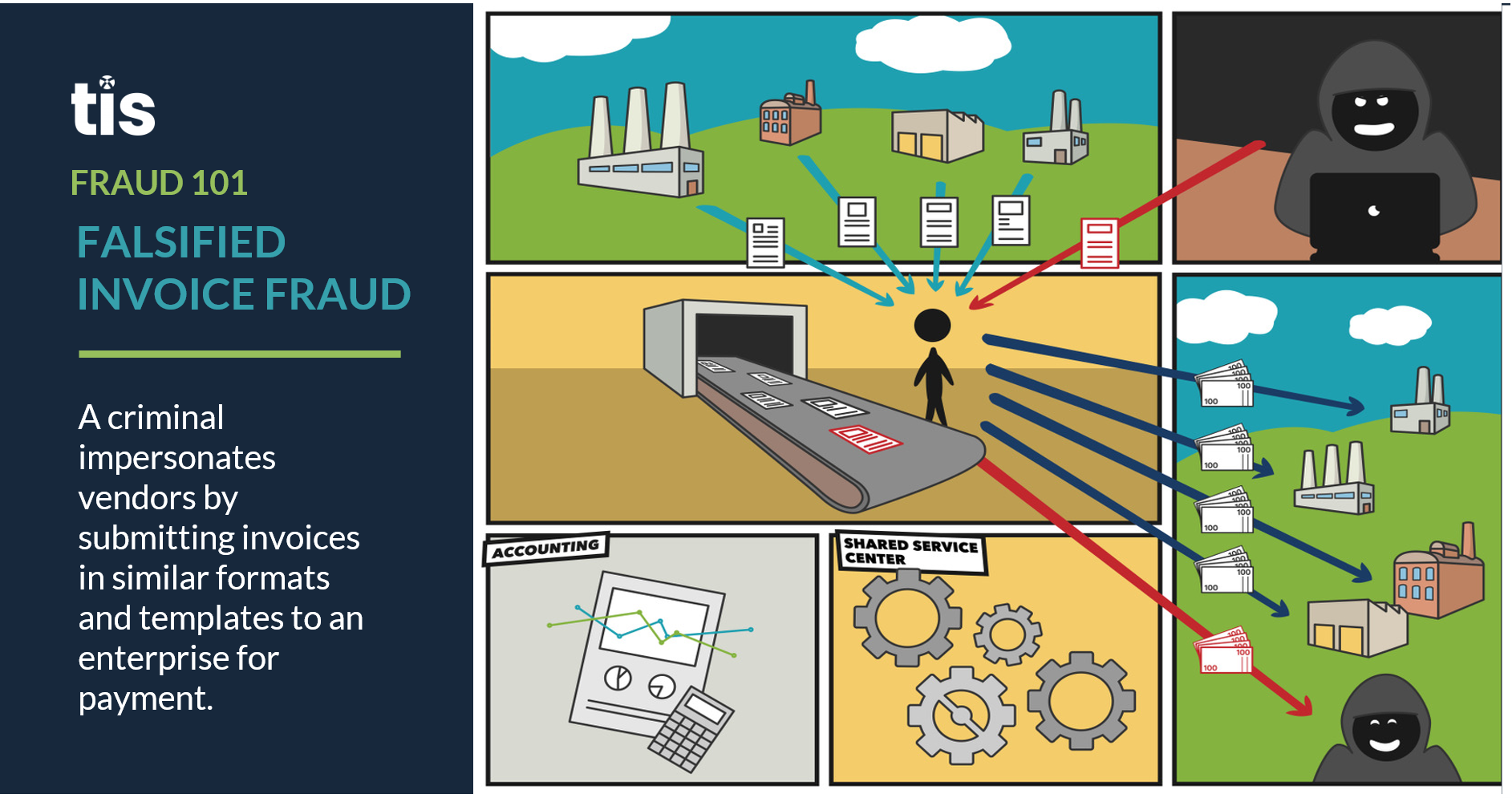
- Fake Invoices / Payment Requests. Whether it’s by submitting altered invoice requests or issuing fraudulent checks, a majority of the external payment fraud attempts experienced by AP teams occur within this realm. As demonstrated by the visual below, fake invoicing and payment requests are typically carried out by a rogue actor that understands an enterprise’s general workflow for receiving and processing invoices. Perhaps a vendor account or employee email is compromised, and the criminal is able to observe the back-and-forth between vendors and AP teams as invoices and payments are processed.As the AP team goes about standard operations, this actor will bide their time before strategically submitting false invoices that mimic those provided by an existing vendor, and will likely use a similar email address, communication style, invoice template, and payment amount. The only difference in the invoice will be the beneficiary details or bank account information. The intent is to submit these invoices subversively and hope that, in the midst of submitting thousands of invoices per week, an AP team will simply overlook the discrepancy and not notice that an error has occurred until it’s too late. In recent years, high-profile schemes of this nature have been carried out against Amazon and other large enterprises, with losses adding up into the millions of dollars.

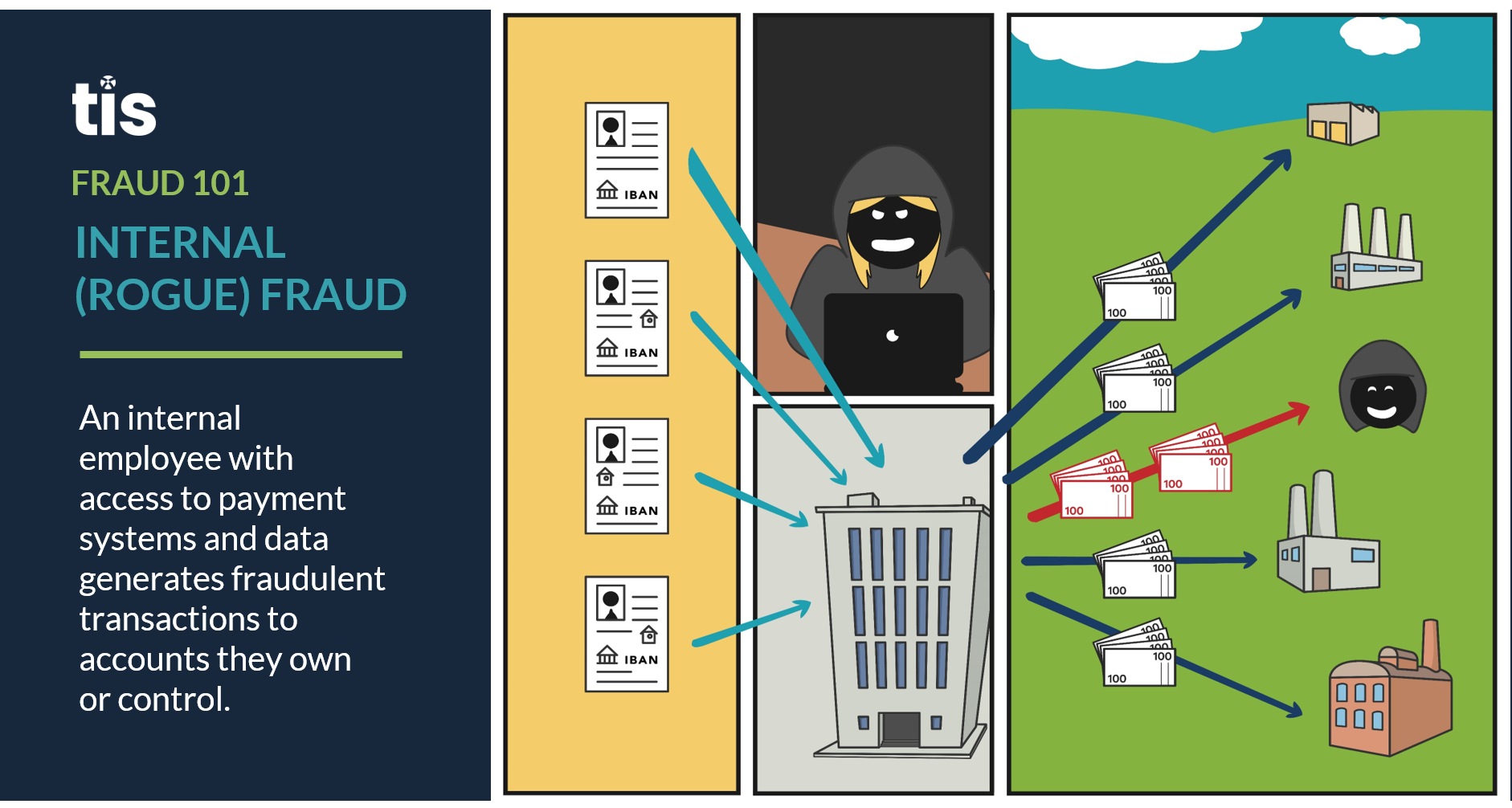
- Internal Fraud / Employee Malpractice. As is the unfortunate reality today, there are a variety of AP fraud attempts that are perpetrated from the inside. In fact, a 2020 survey found that fraudulent billing attempts, the main source of fraud experienced by AP during that year, were most commonly orchestrated by active employees. Common examples of internal fraud today include fake invoices that are generated to shell companies owned by an employee, as well as the use of inactive vendor accounts to submit fake invoice requests with altered bank account details that are employee-owned. Because AP employees have an innate working knowledge of their enterprise and are familiar with the various security and defense protocols in place, those that choose to act illicitly are often best equipped to bypass existing controls in order to extract funds. As a result, internal AP fraud remains a major problem for enterprises today.

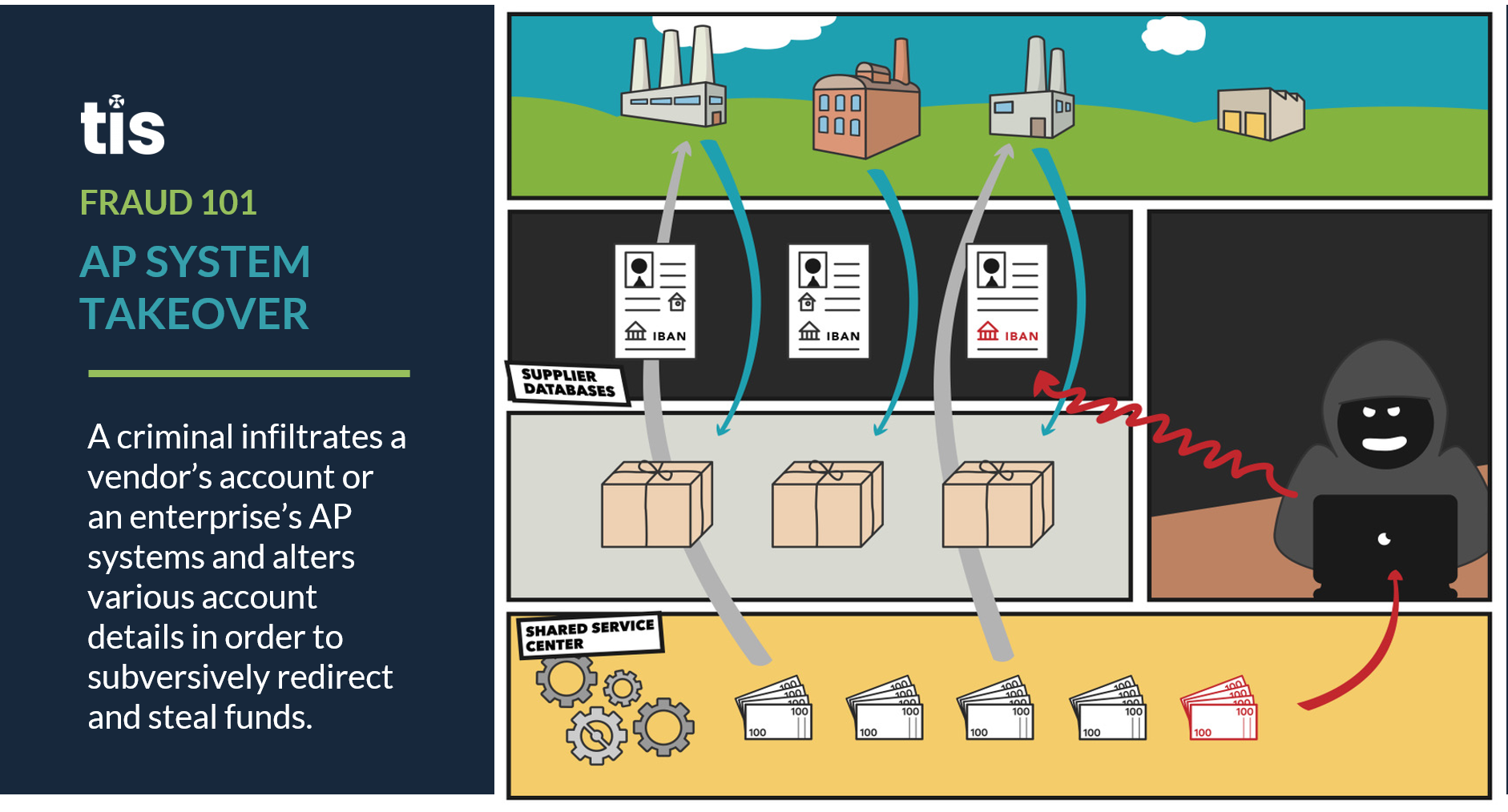
- System Takeover / Vendor Record Changes. Although the above two AP fraud schemes certainly require an element of technology prowess on behalf of criminals, the most tech-savvy fraudsters are learning, either through phishing, BEC, malware, or brute force attacks, to exploit loopholes in an organization’s software security and gain access to their central systems. Often, these types of attacks ultimately result in ransomware and malicious bugs being uploaded to the enterprise’s systems in order to shut them down, but criminals are also learning that going unnoticed within the system for as long as possible has its own benefits.
For instance, where AP is concerned, a criminal with access to the central system can review the enterprise’s vendor master file and make subtle changes to invoice details, account numbers, and beneficiary details, which can go unnoticed for extended periods. The result is that criminals can submit numerous false invoices for payment that are not being flagged internally. Although this is perhaps the most difficult form of fraud for criminals to perpetrate, it is also perhaps the most lucrative, and organizations must institute multiple layers of defense in order to protect against a system breach of this kind.
So then, given the variety and multifaceted set of AP attacks that are being perpetrated against enterprises today, what specific set(s) of tools should be deployed in order to prevent losses from occurring?
What Tools & Tricks Can AP Teams Deploy to Help Defend Against Modern Fraud?
Thankfully, just as criminals go more sophisticated and advanced in their tactics used to perpetrate fraud, enterprise defenses and security practices have grown more robust in tandem. In 2022, five of the most useful security tools and tricks for preventing AP fraud are highlighted below.
- Vendor Master File Control & Invoice Auditing Software. To help protect against the general threat of vendor master file tampering, as well as the submission of duplicate or fraudulent invoices, AP teams should look to adopt system auditing software that can keep track of any and all changes submitted to the vendor master file. The leading vendor management and invoice auditing software can simultaneously track vendor record changes and also check for duplicate invoice numbers or invoices with suspicious amounts and beneficiary details. Generally, these solutions are a best practice in the modern AP environment because they help ensure the integrity of an enterprise’s vendor data and all associated invoices.
- Regular & Intensive Employee Training. In practice, many technological components of security only work as long as the AP personnel that leverage them are aware of how to use them. For instance, if an employee forgets to install multifactor authentication on their account or forgets to delete old employee or vendor credentials from their system, the company can be exposed to significant risk. And if multiple employees are negligent in following the company’s security policies, the threat of an actual loss is quite real. For this reason, corporates must develop an intentional strategy to routinely educate their employees about fraud and cybercrime, especially for those that have access and authority over payments, data, and invoicing systems. This education should cover the latest threats from fraudulent actors, as well as best practices for utilizing the security systems the corporate has in place to prevent and detect attacks.
- Segregation of Duties & User Audit Logs. Should a fraudster or rogue employee illicitly gain access to your enterprise systems, there are still a variety of preventative measures that can be deployed to stop them from physically extracting funds. One of the most common involves the use of dual controls, which is simply a mechanism for ensuring that the execution of a transaction or processing of a payment requires authentication by multiple employees. This is so that a single user cannot manage the entire payments or invoicing lifecycle on their own. By requiring 2-3 employees to review and approve each payment before it is executed, the risk of a single actor being able to fraudulently withdraw funds is largely eliminated.In addition to dual controls/segregation of duties, one of the leading methods used to detect fraud is through the use of system-wide user auditing software. User auditing controls have become a core component of many corporate payment systems today because they keep a complete log of every action carried out by each specific user on the platform. This includes what information they enter, what times they log in, and what screens and dashboards they visit. This way, administrators and compliance teams have complete transparency into evaluating potential fraudulent actions that occur through any specific user account.
- Payee Community Screening (PCS). Developed in direct response to a noted increase in payments fraud, TIS’ newly-released PCS solution works by aggregating payments data across our trusted community of global enterprises and bank partners. As new payment requests are submitted to an enterprise by various vendors, suppliers, and partners, the PCS module compares the underlying beneficiary and bank account information against a comprehensive record of all other transactions executed through the system, including those made by other enterprises in the network.In practice, this validation process effectively protects against four fundamental threats:If you are making payments to a new beneficiary or bank account for the first time, an alert will be generated by the system warning you that an additional review of the information is recommended.If you are making payments to a beneficiary that is completely unknown to other members of the PCS network, then the payment is flagged and a review workflow is initiated.For new vendors that you are paying for the first time, if the invoice and payment details do not match what other enterprises in the network have used to pay the vendor (i.e. a different bank account number was provided to your enterprise than what was provided to other enterprises in the network), then the payment is flagged and a review workflow is initiated.
If the beneficiary or bank account details provided in an invoice ever match with a known criminal, sanctioned, or otherwise fraudulent party, the payment is automatically flagged and a review workflow is initiated.
- Standard Multifactor Authentication (MFA), Firewalls, VPNs, & IP Security Protocols. Finally, as a general layer of more standardized controls and security options, enterprises should always strive to ensure the encryption and integrity of their online software “perimeter”. In practice, this includes the adoption of firewalls and internet security systems, as well as IP safe-listing and VPN access for users logging into company platforms, especially from remote locations. At the same time, protecting user credentials through multifactor authentication (MFA) tools that require numerous forms of identification during login is particularly useful for ensuring user credentials are not easily jeopardized.
Next Steps for Enterprises Wanting to Optimize the Security of Their AP Function
When all the above security tactics and technologies are adopted in-tandem with one another by an enterprise, they have proven very successful at preventing AP fraud attempts from both internal and external sources.
Of course, much will rely on the ability of the enterprise’s staff to properly utilize the tools at their disposal, so training is vitally important.
However, once the proper solutions are adopted across the company, AP groups will be able to monitor all of their team’s individual system actions, as well as all associated invoicing workflows, payment processes, and data transmissions globally. They will also be able to identify fraudulent threats in real-time, halt and review suspicious invoices and payments, and inspect all of the transaction details for every payment initiated through their systems. Ultimately, this multifaceted approach to security will create an environment where criminals must obtain multiple forms of verification and identification in order to perpetrate fraud, which makes it exponentially harder for them to target your firm.
Although the adoption of the aforementioned security features is rising fast across the corporate landscape, there are still many organizations that remain stuck with archaic security systems that expose their AP invoicing and payment workflows to significant risk. In a world where the majority of AP, treasury, and finance teams are operating remotely, an outdated digital security architecture is simply no longer acceptable. In the modern era, corporates must implement numerous layers of digital security to keep their assets safe. And if you feel your company is lagging behind, it is vital that you act before it is too late.
For more information about how TIS can help you manage global payments security, request a demo or learn about the full scope of our solutions.