This article provides a modern review of the tactics used by cyber criminals to target enterprises with fraudulent schemes and also evaluates the primary methods used by companies for defending against digital payments fraud. This is followed by an introduction to TIS’ innovative Payee Community Screening (PCS) solution, which addresses payments fraud on a global scale by curating a community-based network of trusted beneficiaries, vendors, and bank account information that enterprises can use to verify the legitimacy of their outbound payment instructions.
Enterprise Payments Fraud in 2021 is More Elaborate & Subversive than Ever Before
Within the past year alone, thousands of finance and treasury practitioners across the world have learned through bitter experience that digital payments fraud is rarely orchestrated by your average, everyday criminal.
Rather, the vast majority of today’s technology-oriented attacks, particularly those that target large enterprises, are led by sophisticated, well-funded, and innovative fraudsters.
In many cases, these software-savvy perpetrators are working on behalf of state-sponsored actors or underground “black-hat” organizations. And because these groups are well-organized and well-funded, they can provide members with the latest technology and training. Ultimately, this has led to rapid digital innovation within the criminal underworld, and subsequently to a growing frequency of highly-orchestrated payments fraud attacks against the corporate environment.

Consisting primarily of software hacks or malware attacks, many of the most prevalent forms of fraud in existence today involve numerous layers of subterfuge and deception, which is necessary for bypassing the various security controls that organizations have in place. Common examples include the use of cleverly disguised Business Email Compromise (BEC) schemes, “Man-in-the-Middle” tactics, invoicing fraud, and the use of ransomware or other forms of “system takeover” fraud.
But of course, enterprises are not entirely helpless in defending themselves.
What Payment Security Tools Does a Modern-Day Treasury Group Utilize?
If you’re operating in a role with direct access or authority over an enterprise’s outbound transactions, you could probably name a broad number of tools at your company’s disposal for detecting and preventing payments fraud.
Some quick examples?
When initially establishing internal payment protocols, most companies will require clear segregation of duties between each stakeholder in the payment process. This includes dual or multi-user approval controls for executing, reviewing, and approving payments. Other standard security components, such as the use of encrypted Wi-Fi networks or VPNs, help restrict access to the enterprise’s digital software to only trusted sources. IP safe-listing tools provide even greater control over who can access these internal systems. As users log in, configuring multifactor authentication (MFA) tokens to be used in conjunction with standard usernames and passwords is another effective technique that prevents unauthorized users or personnel from accessing payment systems via stolen credentials. Biometric versions of these MFA tokens, such as fingerprint or retinal scanners, may be leveraged for even greater security. And finally, user auditing software is often adopted by companies to help monitor the activity of various personnel within their payment systems in order to detect suspicious activity, such as a login attempt from an unknown IP address, at an odd time of day, or from an obscure world region.
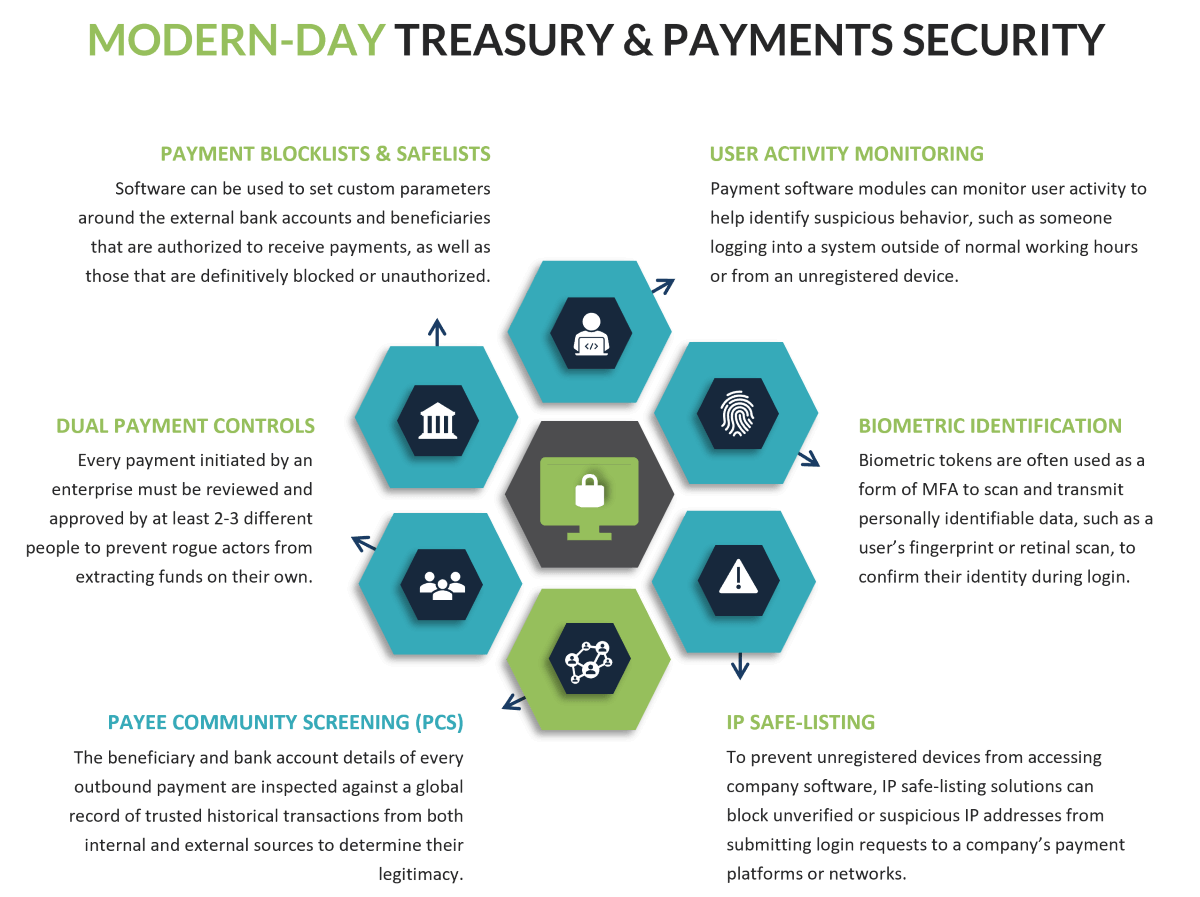
When all combined together with regular employee testing and training, these various security techniques have proven very effective for combating most forms of digital treasury and payments fraud in existence today. And in the years ahead, these tactics are expected to remain as core features of most enterprise’s fraud prevention strategies.
However, suppose that the criminals targeting your organization are not launching direct attacks against your internal payment systems or architecture, but instead decide to infiltrate the operations of your suppliers and partners.
Their reasoning?
Although your enterprise might have the appropriate defenses in place for preventing direct hacks and internal breaches, are your controls just as effective at identifying anomalous activity that is perpetrated through the guise of a trusted vendor?
For a surprising number of enterprises today, the simple answer is no.
Successful Fraudsters Learn How to Operate Outside the Purview of Enterprise Visibility
Although many of the fraud attacks that garner widespread media attention are those that result in millions or billions of losses in a single swoop, these are not the only types of attacks that organizations should be worried about.
In reality, many of the attempts perpetrated by criminals are not targeting billions of dollars. Instead, they focus on extracting smaller amounts of funds over time, often by disguising their activity through the lens of normal business operations.
Take, as an example, fake invoices submitted by criminals that are designed to mimic one of the thousands of vendor or supplier payments that a global enterprise makes every month.
Common Payment Fraud Types
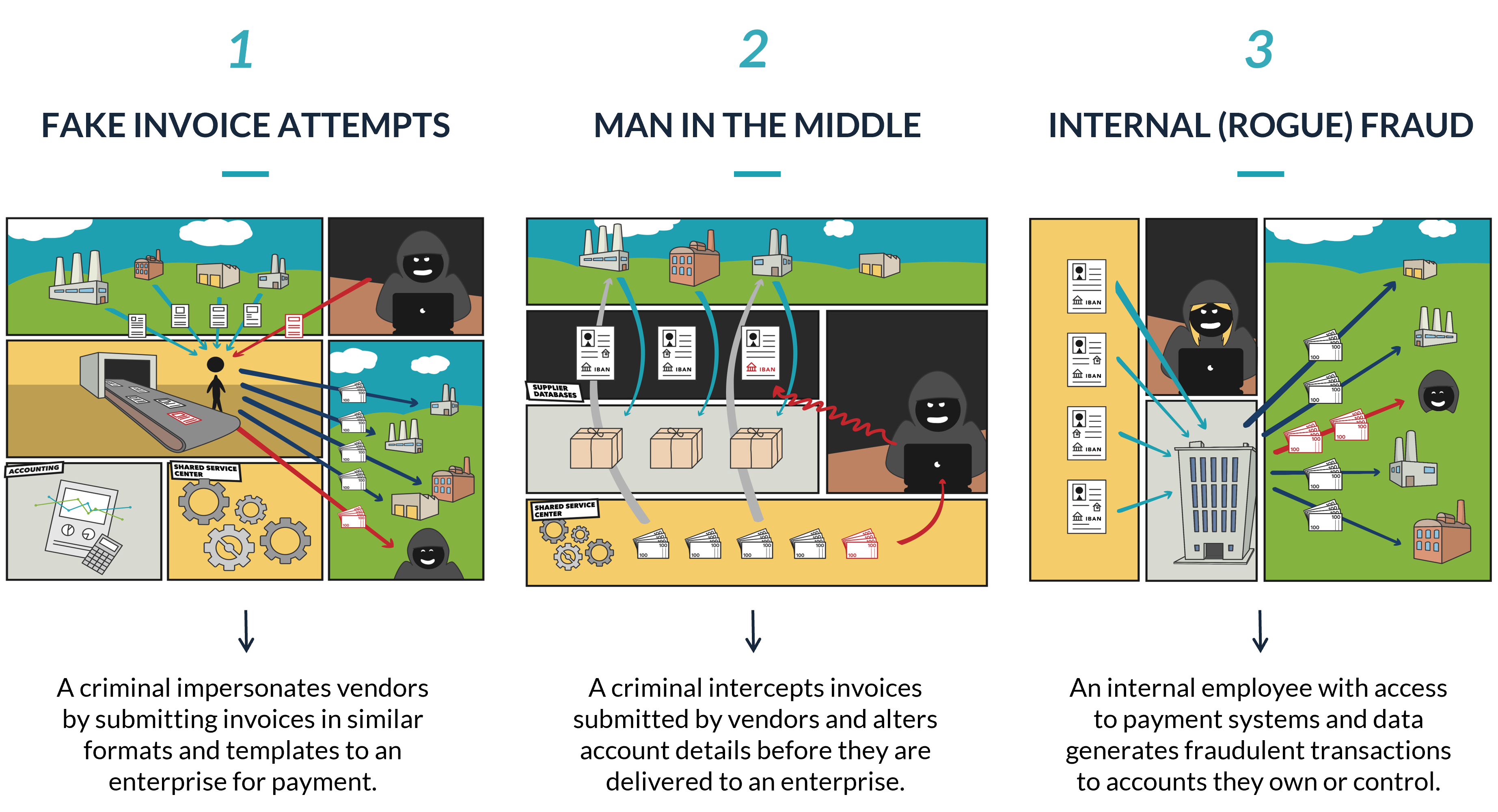
Usually, vendors are submitting invoices to enterprises via email, an online e-commerce platform, or via an ERP system. Subsequent payments are then delivered from the enterprise to the various recipients whose invoices have been approved, usually as an account-to-account transaction that goes directly to the bank account listed in the invoice.
However, suppose that a criminal is able to infiltrate the email account, e-commerce platform, or payment system used by one of your vendors. And over time, the criminal monitors the activity and communication that occurs between this vendor and your enterprise and learns how to mimic the workflow, presentation, and delivery of new invoices for payment.
In this scenario, the criminal knows that your company is receiving hundreds, if not thousands, of new invoices from a variety of vendors every day. They also know the average dollar amount of each invoice delivered by particular vendors, as well as the frequency and timing of their submissions. And if an email account or e-commerce platform has been hacked, they have also probably been studying the language and messaging that the vendor uses to correspond with you.
After taking time to evaluate these invoicing and communication processes, the criminal will create a falsified invoice using the same email address or payment platform that you’re familiar with. The invoice will probably be for the same amount and to the same beneficiary that you’re used to paying, but with a slight variation to the underlying bank account details.
The typical result being?
Unless you are actively tracking and inspecting the vendor records, bank account numbers, and beneficiary details for EVERY payment initiated by your enterprise to your global network of partners and vendors, then catching these attempts will be incredibly difficult.
But if your company cannot catch this errant invoice the first time, then what is going to stop the criminal from submitting numerous invoices over and over, or even going on to target other vendors within your network and duplicating the process on a broader scale?
It might sound like an Ocean’s 11 heist on paper, but in reality, these types of attacks occur all the time. In fact, a single instance of invoice fraud cost Amazon nearly $20 million in 2020. Other forms of fraud, such as BEC schemes, cost a combined $12.5 billion for organizations in the same timeframe, and these numbers are not decreasing over time.
Instead, they are continuing to rise.
Introducing a New Way to Quickly Identify Suspicious or Fraudulent Payment Details
Although subversive types of fraud attacks like the invoice example above are difficult for large companies to identify, suppose there were a way to quickly scan all vendor and supplier payments in real-time against a global library of beneficiary and bank account data?
Going a step further, what if you could also scan outbound transactions being delivered to first-time vendors against a community ledger of payments data in order to verify that the underlying account details and remittance info have never been flagged as suspicious or fraudulent by other enterprises?
With this functionality, the threat of fraud being perpetrated through more obscure and subversive channels become much easier to identify, and they go a long way in protecting your enterprise against attacks that spawn through exposures related to your partners, vendors, and suppliers.
This suite of tools is exactly what TIS is now providing enterprise clients with our innovative Payee Community Screening (PCS) solution.
Developed in direct response to a noted increase in invoice and BEC fraud, TIS’ PCS network works by aggregating payments data across our trusted community of global enterprises and bank partners. As new payments are submitted by various enterprises through TIS, this module compares the underlying beneficiary and bank account information against a comprehensive record of all other transactions executed through the system, including those made by other enterprises in the network.
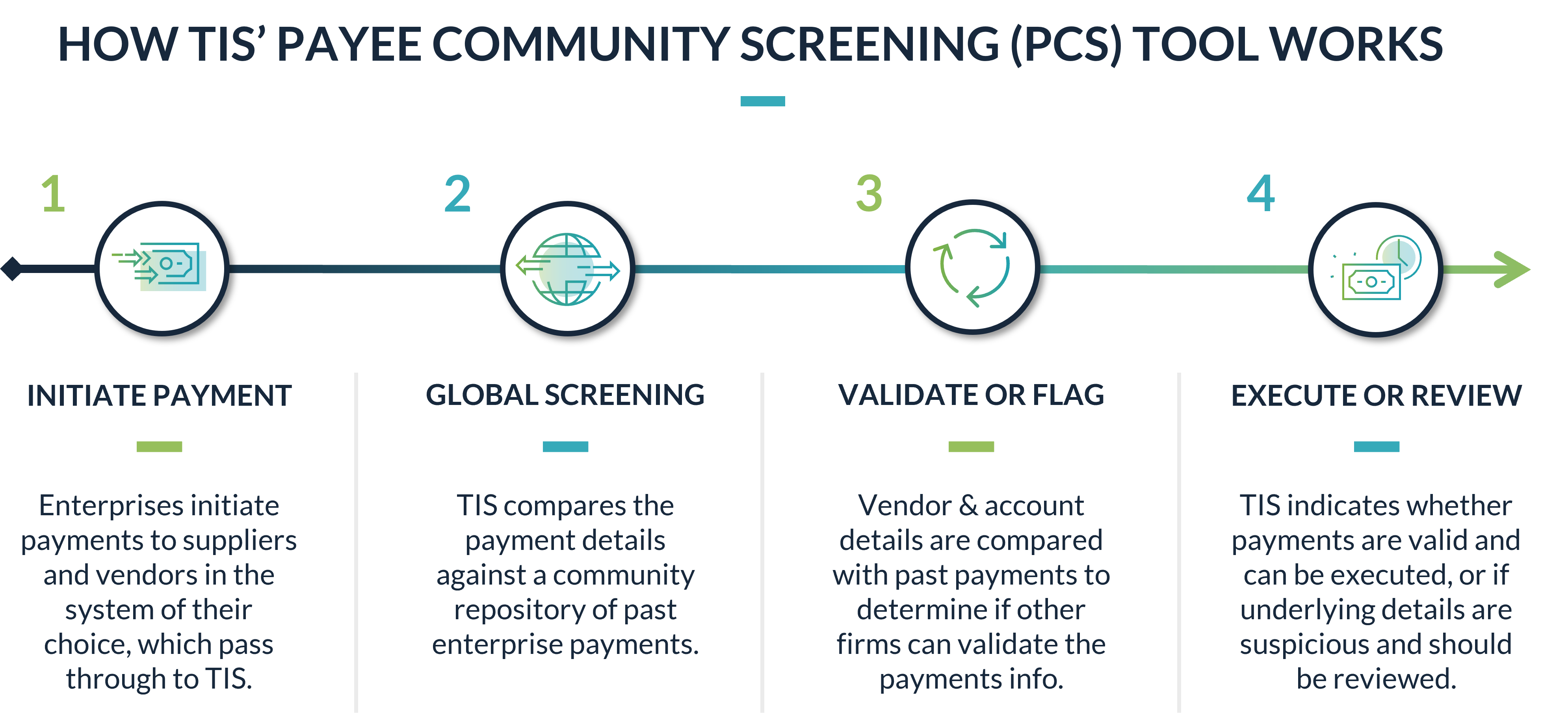
In practice, this validation process effectively protects against four fundamental threats:
- If you are making payments to a new beneficiary or bank account for the first time, an alert will be generated by the system warning you that an additional review of the information is recommended.
- If you are making payments to a beneficiary which is completely unknown to other members of the PCS network, then the payment is flagged and a review workflow is initiated.
- For new vendors that you are paying for the first time, if the invoice and payment details do not match what other enterprises in the network have used to pay the vendor (i.e. a different bank account number was provided to your enterprise than what was provided to other enterprises in the network), then the payment is flagged and a review workflow is initiated.
- If the beneficiary or bank account details provided in an invoice ever match with a known criminal, sanctioned, or otherwise fraudulent party, the payment is automatically flagged and a review workflow is initiated.
In this way, by inspecting every outbound payment initiated by your enterprise in real-time against a global library of payments information, enterprises can strengthen their security controls by accessing a much broader pool of data and information than what is available in-house. With the addition of PCS to our solution suite, we can better protect our enterprise clients from fraud by confirming the validity of every outbound transaction they are attempting to make.
In an environment where subterfuge and deception are a criminal’s main assets, these community screening techniques are essential for ensuring that fraudsters cannot bypass your controls simply by infiltrating those of a different company within your network. They also ensure that as soon as fraudulent or suspicious payment info is identified by one enterprise, the data can be quickly shared across all other enterprises in the network for purposes of quickly halting subsequent payments to that account or beneficiary.
For TIS’ enterprise clients, these tools are already becoming a pivotal component of their core security structure, and we are excited to continue deploying the solution across more global enterprises in the months and years ahead.
Learn More About How PCS Can Bolster Your Treasury & Payments Security
Although no single tool should ever be relied upon to defend against all forms of fraud, it is strongly recommended that enterprises making hundreds or thousands of vendor payments every day undergo a thorough evaluation of their payment controls. More specifically, treasury and AP teams should take time to analyze whether the threat of invoice or BEC fraud leaves them exposed, especially if a vendor or supplier within their network is compromised.
For enterprises that identify gaps, we invite you to learn more about how TIS can help.
For more information about TIS’ PCS tool, the associated benefits, and the technical aspects associated with its architecture, download our latest factsheet. You can also request a meeting with one of our payment experts or learn more about the other security-related components of our solution suite.
Stay vigilant, stay safe, and as always, thank you for reading.
Click here to review TIS’ data and legal policy as it relates to the use of our PCS Solution.



